Zyxel OneNetwork Utility V2.1.4C0
Towards the end of last year I reported a privilege escalation vulnerability to Zyxel which was found in their OneNetwork Utility which has now been fixed.
This issue was easy to find and demonstrates the importance of validating applications for low hanging privilege escalation vectors.
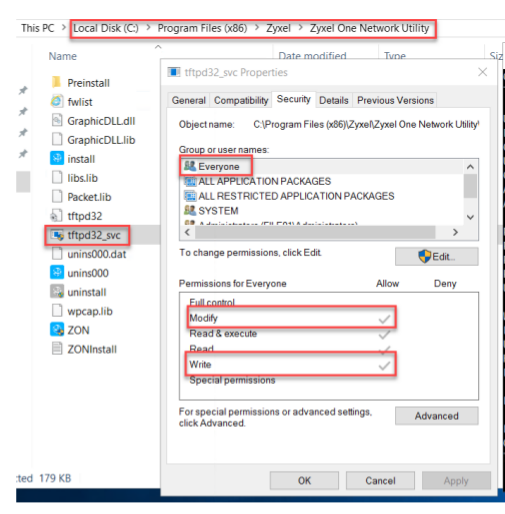
On installation, the application has weak folder permissions configured. It can be seen from the graphic below that the ‘Everyone’ group has ‘write’ privileges on the installation folder/files.
This would allow a malicious attacker with a standard low privileged user account to replace the binary ‘tftpd32_svc’ which runs as SYSTEM with a malicious binary and elevate their privileges to SYSTEM once the application/service is launched.
This issue was reported to the Zyxel security team, they responded quickly and released a patch quickly too. In addition they kept me informed of their actions throughout the process.
